Fuzz Testing
Fuzz is an automated, open-source software testing technique that security researchers, developers, and organizations use to determine security vulnerabilities, bugs, and flaws in software applications.
Professor Barton Miller introduced this automated testing mechanism in the 1980s with the intention of breaking software applications in order to enhance their stability and security.
Nowadays, you may see significant growth around fuzz testing as it helps deliver more robust and free-to-use testing options. In addition, these tools are typically preserved and updated by businesses (e.g., key market leaders such as Google, Microsoft, etc.) and active individual contributors, allowing a high demand and significant popularity across users to grow significantly around fuzz testing.
Understanding How Fuzz Testing is Done
Fuzz testing involves injecting unexpected, random, or malformed data into a system to observe its reactions and behavior. This approach helps uncover issues such as security vulnerabilities, logic errors, crashes, memory corruption, concurrency problems, and input validation flaws.
Here are detailed steps on how to carry out fuzz testing:
- Step 1 – Input generation: The fuzzer (the program that injects data) produces a substantial amount of random, malformed, or unexpected inputs that may differ in their data types.
- Step 2 – Test execution: The produced inputs are then injected into the software, which could be an application, library, or service.
- Step 3 – Monitor the system: The fuzzer monitors how software behaves or reacts and will try to discover crashes, memory leaks, buffer overflows, exception handling failures, etc.
- Step 4 – Bug identification and analysis: Once a failure is discovered, the fuzzer logs the input and will trigger a detailed analysis of the issue, assisting developers in identifying which part of the software has failed and why.
- Step 5 – Reproduce and fix: Once vulnerabilities are identified, developers reproduce and fix them.
Fuzz Testing vs. Penetration Testing
Both fuzz and penetration testing are essential techniques in identifying vulnerabilities and enhancing the security of software applications. However, they serve different purposes, have distinct methodologies, and excel in complementary areas.
While fuzz testing excels at identifying system vulnerabilities caused by invalid or unexpected inputs, penetration testing focuses on simulating attack scenarios to uncover exploitable weaknesses. For comprehensive security, combining fuzz testing with penetration testing ensures both automated edge case coverage and real-world threat validation.
Best Practices in Fuzz Testing
- Target essential elements: Customize fuzz inputs to increase the chances of triggering vulnerabilities like APIs, network protocols, or file formats.
- Use coverage-guided fuzzing: Assure the fuzzer executes a wide variety of input values, which includes edge cases, boundary conditions, and invalid inputs.
- Log and categorize failures: During fuzzing, the team must ensure any crashes or issues detected can be reproduced easily and analyzed in a timely manner. Logging these inputs and conditions that lead to failure benefits the teams in the long run.
- Automate repetition: Fuzz tests must be automated to run continuously throughout the lifecycle to detect bugs or issues and ensure any code changes do not introduce regressions.
- Classify bug-fixing order: Focusing on critical areas that are most exposed to user input, such as network interfaces, file parsers, or web forms, and fixing them based on priority will improve the effectiveness of software applications.
- Monitor other impacted areas: It’s also important to monitor other problematic behaviors, such as memory leaks, unhandled exceptions, or unexpected resource consumption.
- Combine fuzz testing with other testing techniques: For robust detection of vulnerabilities, fuzz tests should be combined with other testing methods like code reviews, static code analysis, and penetration testing.
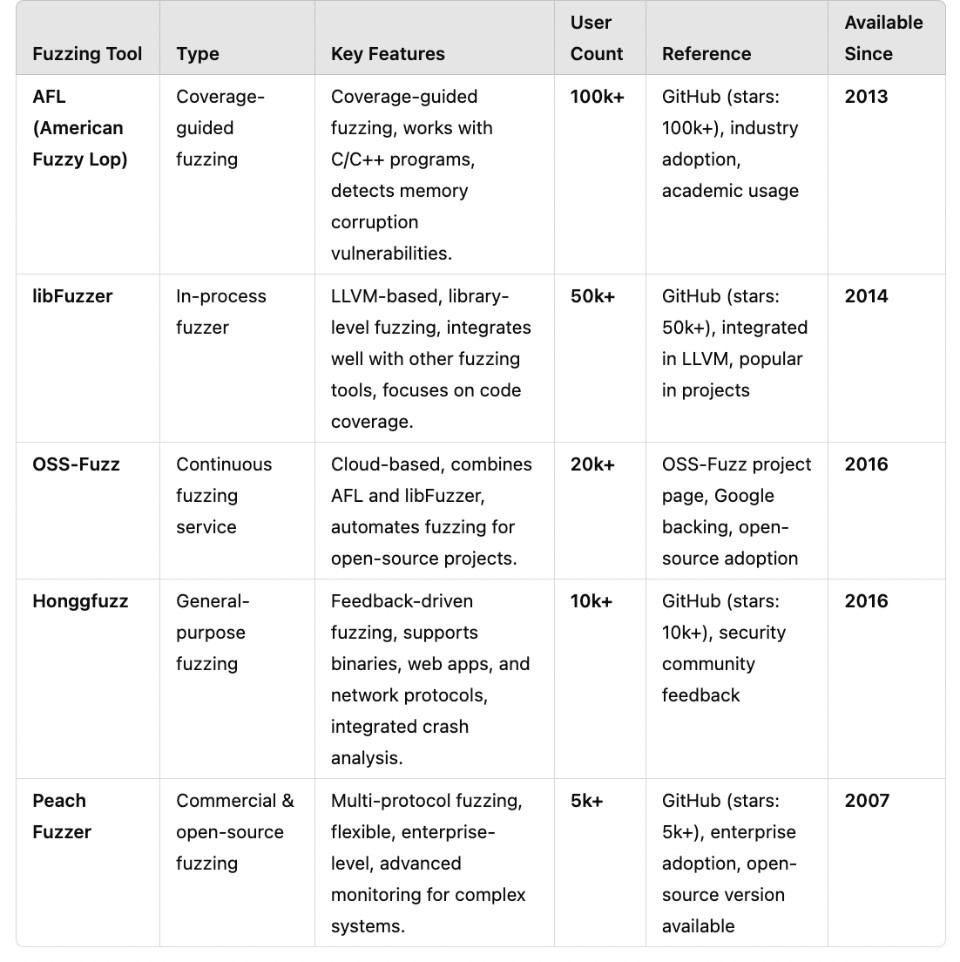
Most Popular Open-Source Fuzz Testing Software Tools
Based on popularity, the top 5 fuzz testing software as of 2024 are AFL, LibFuzzer, OSS-Fuzz, Honggfuzz, and Peach Fuzzer.
As shown above, AFL has been used by more than 100k users since 2013 and is by far the best tool available that specializes in coverage-guided fuzzing.
Benefits of Fuzz Testing
- Rapid discovery of security vulnerabilities: Uncovers most critical security flaws that could be overlooked by other testing methods.
- Automated testing capability: Fuzz testing facilitates automation, which allows repetition, continuous integration, and regular testing.
- Wide coverage: Can be used for a wide range of input combinations covering edge cases that may be missed by human testers.
- Security Testing: Extremely effective at discovering security-related issues that are difficult to discover with other security test methods.
- Low cost: Detecting bugs earlier significantly reduces the costs of having to fix vulnerabilities later in the development cycle.
Challenges of Fuzz Testing
- High false-positive rate: Fuzz may generate a higher number of false positives, which may require additional effort to resolve.
- Narrow scope: As fuzz testing is not involved in logic-based vulnerabilities, it may not effectively test every aspect of an application.
- Complex input generation: It is a rigorous task to create effective input generators for complex protocols or file formats.
Summary
While many testing techniques are available in modern software development, Fuzz testing has emerged as an invaluable tool that offers robust benefits in discovering critical vulnerabilities.
Fuzz testing has many more benefits than challenges, however, as it is an efficient testing method that facilitates edge case detection and early discovery of security flaws, which helps enhance overall software security and reliability. When strategically implemented, fuzz testing is a crucial component in building more resilient applications.